Panoptoで安全な動画管理
Panoptoは、お客様のデータのセキュリティ、機密性、完全性、およびプライバシーを保護するための厳格なセーフガードを維持しています。








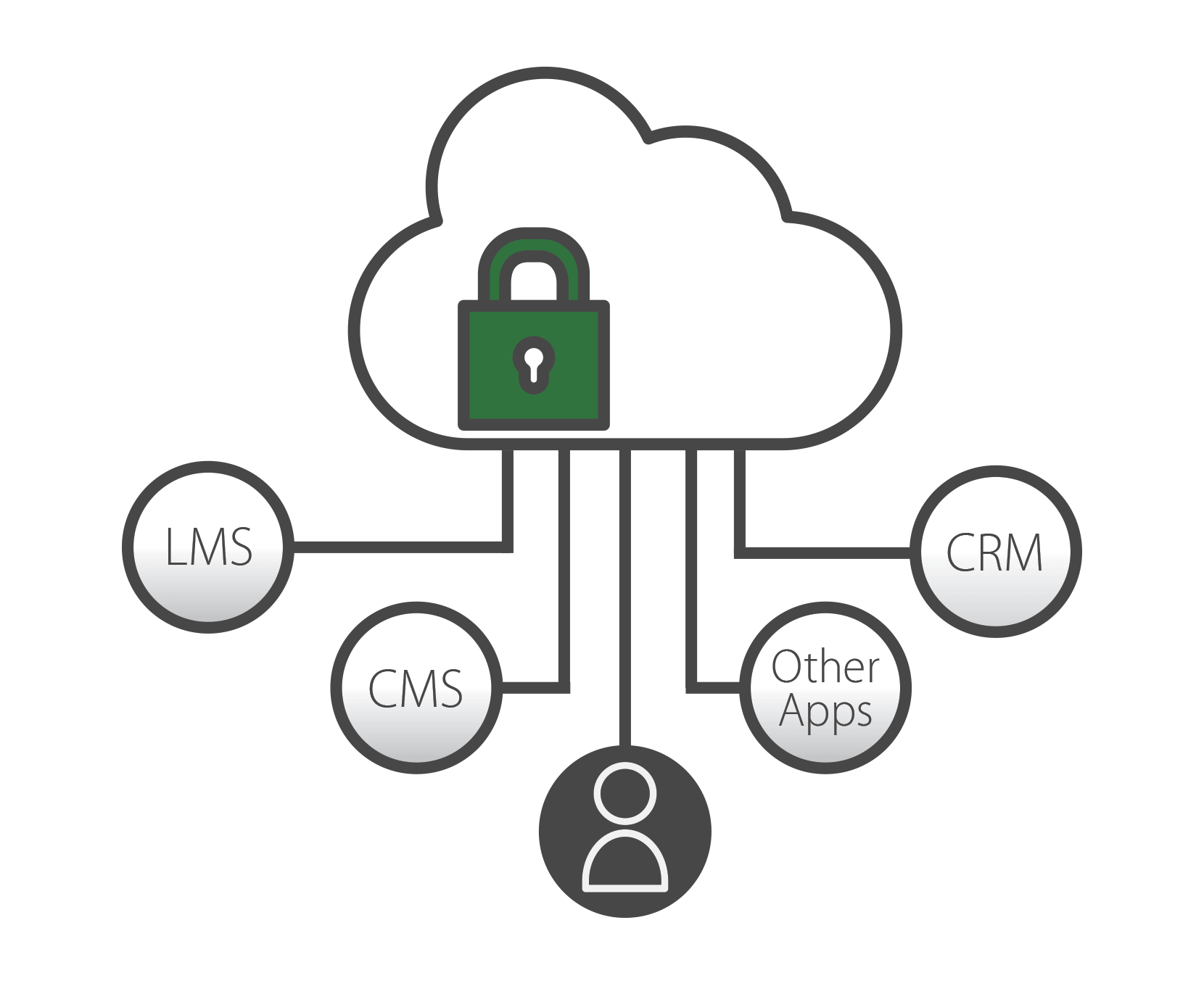
当社の共有セキュリティモデル
PanoptoはSaaS(Software-as-a-Service)モデルを採用しており、セキュリティはAmazon Web Services(AWS)、Panopto、およびお客様の間で責任を共有しています。Panoptoはクラウド・インフラストラクチャ・プロバイダとしてAWSを活用し、高可用性、スケーラビリティ、およびセキュリティを備えたソリューションを提供しています。高いレベルでは、AWSは物理的、ネットワーク、および仮想化プラットフォームのセキュリティに責任があります。Panoptoは、ホスト、ミドルウェア、アプリケーションレベルのセキュリティ、イベント監視、ディザスタリカバリに責任を負います。お客様は、ユーザーのアイデンティティ管理、アクセスコントロール、データセキュリティに責任を負います。

セキュリティとプライバシーを重視する企業文化
Panoptoのセキュリティとプライバシーへの取り組みは、採用プロセスから始まり、従業員の入社時、継続的なトレーニング、意識向上のための全社的な取り組みまで、組織文化に根ざしています。誰かがPanoptoチームに加わる前に、現地の法律や規制が許す限り、犯罪歴や信用歴の調査を行います。すべての新しいチームメンバーは、情報セキュリティとプライバシーに関する意識向上トレーニングを受けることが義務付けられています。開発者は、採用時およびその後定期的にセキュアコーディングトレーニングを受けることが求められます。セキュリティチームは、セキュリティニュースレター、電子メールアラート、フィッシングテストなど、定期的な啓蒙活動やトレーニングを行っています。
Panoptoは、効果的な情報セキュリティプログラムには強力なガバナンスが不可欠であると理解しています。当社では、すべての部門とチームを代表するクロスファンクショナルな情報セキュリティ協議会を導入し、セキュリティプログラムの監督と戦略的方向性を提供しています。さらに、この評議会は、情報セキュリティポリシー、標準、およびベストプラクティスを会社の業務に統合するために必要なビジネスサポートを推進し、提供しています。

アプリケーション セキュリティ
Panoptoでは録画から再生まで、動画コンテンツの録画・管理・ストリーミングを安全かつ簡単に実行できます。Panoptoは世界中の大企業や著名な大学に動画プラットフォームを提供しており、ユーザーのサインイン方法からネットワーク上での動画保存・配信方法まで、製品のセキュリティに対し多額の投資を行ってきました。
当社の動画プラットフォームは、境界、リポジトリ内、およびストリーミング時に多層のセキュリティを提供します。これにより、許可されたユーザーのみが動画を視聴することができ、データは保存中および転送中も安全です。
Panoptoは、OAuth、SAML 2.0、Active Directory、および多くのLMS IDプロバイダを含む複数のクレデンシャルタイプをサポートすることで、ビデオリポジトリの境界を保護します。私たちのシングルサインオン(SSO)実装は、資格情報のローリング双方向同期をサポートし、ユーザー情報が常に最新であることを保証します。
Panoptoでは、ユーザーはロールベースのパーミッションによって動画、フォルダ、プレイリストを操作し、アクセスします。これらの権限は、グループまたは個々のユーザーに対して設定することができ、動画の録画、ライブストリーミング、アップロード、公開、再生、およびスケジューリングに対する詳細な制御を提供します。さらに、強力なパスワード、パスワードの有効期限、SSOによる2要素認証、セッションタイムアウトなどを管理者が設定することが可能です。

インフラストラクチャ・セキュリティ
Panoptoは、複数のAWSアベイラビリティーゾーンにまたがるハイアベイラビリティーな冗長性のあるクラスターとしてホストされており、単一障害点を排除し、プラットフォームの信頼性を高めています。ウェブ、エンコーディング、データベースの各サーバーは、アベイラビリティーゾーンをまたいでミラーリングされています。アベイラビリティーゾーン全体が停止した場合でも、システムはシームレスに別のゾーンに移行し、ビジネスの継続性とデータの完全性を保護します。
また、AWSは従来のネットワークセキュリティの脆弱性に対しても大きな保護を提供します。例えば、分散型サービス拒否(DDoS)攻撃の脅威は、独自のDDoS保護サービスと、インターネットアクセスの多様性を提供するマルチホームのAWSネットワークによって軽減されます。中間者(MITM)攻撃は、SSLで保護されたAPIエンドポイントによって防止されます。IPスプーフィングは、AWSのファイアウォールにより防止され、インスタンスが自分以外のソースIPやMACアドレスを持つトラフィックを送信することを許可しません。
さらに、AWSは、データセンターにおいて最先端の複数の境界線による物理的セキュリティを維持しています。これは、外部からのアクセスを禁止し、データセンターの正確な位置を共有しないことを含みます。環境面では、火災検知・消火装置、完全冗長化された電源システム、空調管理、電気・機械システムのリアルタイム管理などの対策が施されています。
運用面でのセキュリティ
Panoptoは、リスクベースの情報セキュリティプログラムを運用する基礎として、NIST SP 800-53コントロールフレームワークを採用しています。社内のシステムとプロセスは、アクセスコントロール、リスクアセスメント、意識とトレーニング、サプライチェーンリスクマネジメント、インシデントレスポンス、コンフィギュレーションマネジメント、物理的・環境的保護など、NISTのコントロールファミリーを網羅したセキュリティポリシーによって管理されています。
当社のエンジニアリングチームは、安全なソフトウェア開発ライフサイクルを用いて、コードレビューやアーキテクチャ分析などのセキュリティ保証活動が開発作業に内在するようにしています。
また、四半期ごとに脆弱性スキャンを実施し、クラウドのセキュリティ対策とアクセス権について定期的に内部監査を行っています。毎年、国際的に有名な独立系セキュリティ企業と提携し、包括的なペネトレーションテストを実施することで、悪用可能な脆弱性を特定し、サイバー攻撃の表面積を最小化しています。
さらに、Panoptoは、当社の製品やサービスの脆弱性を特定するために、外部の研究者の支援を重視しています。当社の当社の責任ある開示プログラムでは、ユーザーデータの機密性や完全性に影響を与えたり、顧客データを危険にさらしたりする設計や実装の問題を報告することを研究者に奨励しています。
セキュリティまたは事業継続のためのインシデントが発生した場合には、準備から特定、封じ込め、根絶、回復、根本原因の分析まで、インシデント対応のあらゆる側面をカバーする対応計画を維持します。この計画は毎年実施され、インシデントの影響を最小限に抑え、可能な限り迅速に通常業務を再開するために、対応の訓練を受けたスタッフのチームを確保しています。

プライバシー
Panoptoは、お客様の個人情報を大切に保護する責任を真剣に考えています。私たちのプライバシーへのアプローチは、お客様のデータの収集、使用、配布についてお客様に透明性を提供するという約束から始まります。
EU一般データ保護規則(GDPR)は、透明性・公平性・説明責任というプライバシーの原則に基づいて、
欧州全体のデータ保護に一貫性をもたらしています。
データ処理者として、PanoptoはGDPR法を遵守することを約束します。
個人情報を保護するための暗号化と匿名化の使用、当社のデータ処理の一翼を担うパートナーとの契約、
当社のデータソースのPIIに関する第三者監査・アクセス権・情報・修正・消去・データポータビリティ・
異議申し立て・処理制限の権利の遵守などが含まれます。

コンプライアンス
サービス・オーガニゼーション・コントロール(SOC)
米国公認会計士協会 (AICPA) によって開発された SOC は、セキュリティ、可用性、処理の整合性、機密性、プライバシーの 5 つのトラスト サービス原則に基づいて、顧客データを管理するための基準を定義しています。
Panoptoは、独立した第三者監査法人によるSOC 2タイプ2監査を毎年受けており、セキュリティと可用性に関する信頼の原則にどの程度準拠しているかを評価しています。
- 安全:セキュリティ原則とは、不正アクセスからシステムリソースを保護することを指します。Panopto ではアクセス制御が実施されており、システムの悪用、盗難、データの不正削除、ソフトウェアの誤用、情報の不適切な変更や開示を防ぐのに役立ちます。 Panopto で使用されるネットワークや Web アプリケーションのファイアウォール、2 要素認証、侵入検知などの IT セキュリティ ツールは、システムやデータへの不正アクセスにつながる可能性のあるセキュリティ侵害を防ぐのに役立ちます。
- 可用性:可用性の原則とは、契約またはサービスレベル契約で規定されているシステム、製品、またはサービスのアクセシビリティを指す。 この文脈では、ネットワークのパフォーマンスと可用性の監視、サイトフェイルオーバー、セキュリティインシデント処理が重要だ。
当社の SOC 2 レポートは、あらゆるパートナー、顧客、見込み客に提供されますが、受信者が Panopto との秘密保持契約 (NDA) に署名している場合に限ります。 詳細については、次を参照してください。
Panopto の SOC 3 レポートは、NDA に署名することなく、SOC 2 レポートの重要な情報を簡単に理解できる要約にまとめます。
クラウドセキュリティアライアンス(CSA)STARセルフアセスメント
クラウド セキュリティ アライアンス (CSA) は、業界の実務家、企業、その他の重要な利害関係者の幅広い連合体が主導する非営利団体です。 より安全なクラウドコンピューティング環境を確保するためのベストプラクティスを定義し、潜在的なクラウド顧客がIT運用をクラウドに移行する際に十分な情報に基づいた意思決定を行えるようにすることに専念しています。 Panopto は、Consensus Assessments Initiative Questionnaire (CAIQ) による CSA STAR 自己評価を完了し、その結果を CSA Security, Trust, and Assurance Registry: Panopto – CAIQ (v3.1) に公開しました。
セキュリティチェックリスト
| アプリケーション セキュリティ | Panoptoに付属 |
|---|---|
| API認証と暗号化 | はい。 |
| 認証ポリシー | はい。 |
| データ検証 | はい。 |
| 保存時の暗号化 | はい。 |
| トランジット中の暗号化 | はい。 |
| 監査ログによるフォレンジック分析 | はい。 |
| ホストプラットフォームのセキュリティ | はい。 |
| インフラストラクチャ・アズ・コード(IaC) | はい。 |
| 論理的なコンテンツ分離 | はい。 |
| 中間者攻撃(MITM)防止 | はい。 |
| 境界セキュリティとシングルサインオン(SSO) | はい。 |
| 役割ベースでの権限付与 | はい。 |
| セキュアなクレデンシャルストレージ | はい。 |
| セッションタイムアウト | はい。 |
| 動画ダウンロード防止 | はい。 |
| インフラと運用セキュリティ | Panoptoに付属 |
|---|---|
| 広く認知されたコントロールフレームワークへの準拠 | はい。 |
| リスクマネジメントプログラム | はい。 |
| 従業員や契約者のバックグラウンドチェック | はい。 |
| セキュリティとプライバシーに関する意識向上とトレーニング | はい。 |
| 最小限の特権と職務の分離 | はい。 |
| 機密情報へのアクセスの必要性 | はい。 |
| 安全なソフトウェア開発ライフサイクル | はい。 |
| 運用環境・開発環境・ステージング環境の分離 | はい。 |
| 変則的なイベントの監視と警告 | はい。 |
| 定期的なコントロール評価と脆弱性スキャン | はい。 |
| 年1回の第三者による包括的なペネトレーションテスト | はい。 |
| リスクに応じた脆弱性の優先順位付けを行います。 | はい。 |
| メディアの安全な廃棄 | はい。 |
| 悪意のあるソフトウェアの保護 | はい。 |
| データ損失防止 | はい。 |
| 物理的・環境的コントロール | はい。 |
| インシデントマネジメントの計画とテスト | はい。 |
| 事業継続性と災害復旧の計画とテスト | はい。 |
| 容量とリソースの計画 | はい。 |
| プライバシーとコンプライアンス | Panoptoに付属 |
|---|---|
| 一般データ保護規則(GDPR | はい。 |
| SSAE 18 SOC 2 Type II | はい。 |
| クラウドセキュリティアライアンス(CSA)STARセルフアセスメント | はい。 |