Secure Videos in Panopto
Panopto maintains stringent safeguards that protect the security, confidentiality, integrity, and privacy of your data.








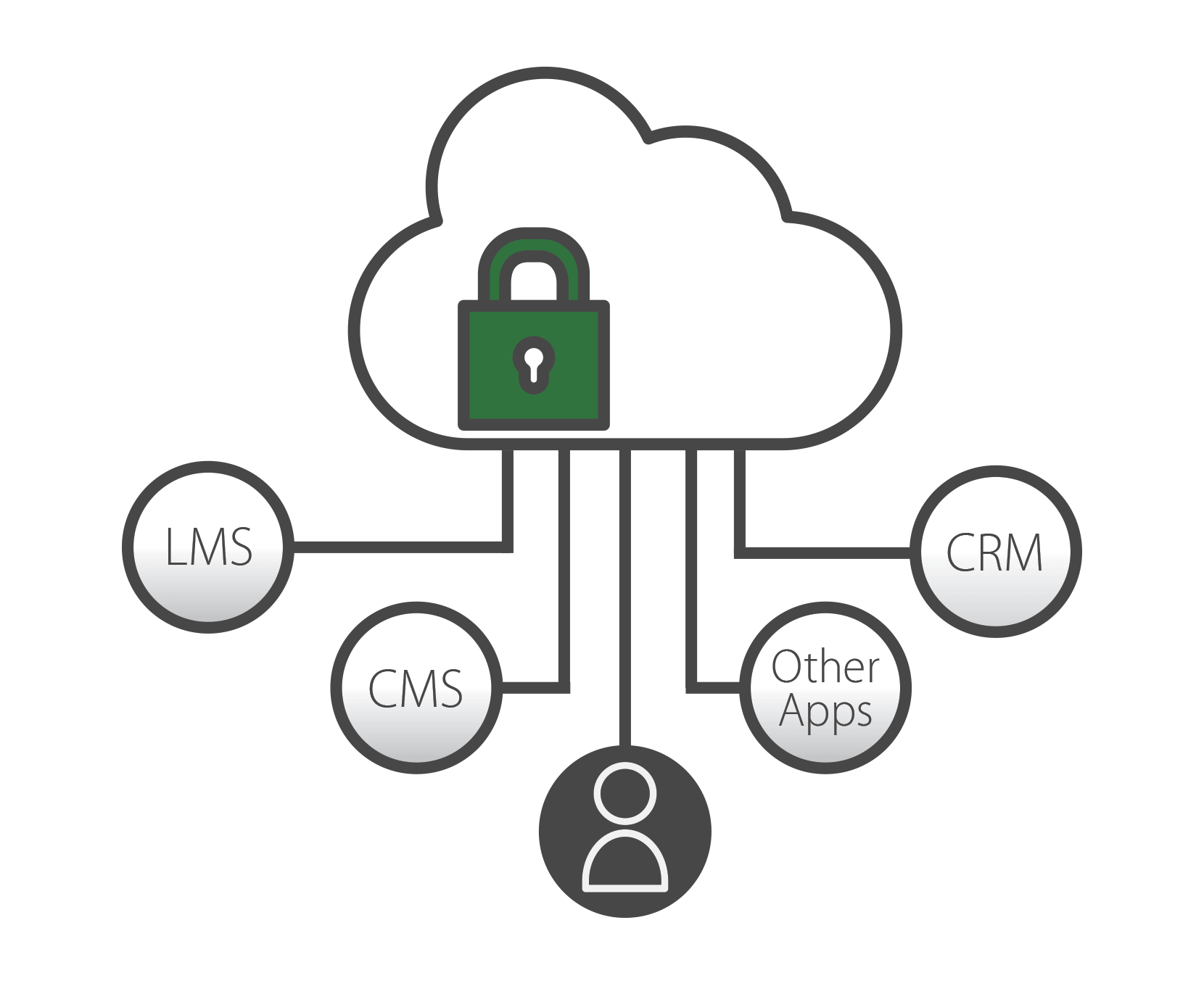
Our Shared Security Model
Panopto utilizes a Software-as-a-Service (SaaS) model in which security is a shared responsibility among Amazon Web Services (AWS), Panopto, and our customers. Panopto leverages AWS as our cloud infrastructure provider to deliver solutions that are highly available, scalable, and secure. At a high level, AWS is responsible for physical, network, and virtualization platform security. Panopto is responsible for host, middleware, and application-level security, event monitoring, and disaster recovery. Customers are responsible for user identity management, access control, and data security.

Security and Privacy-Driven Culture
Panopto’s focus on security and privacy is rooted in our organizational culture, beginning with the hiring process, continuing during employee onboarding, ongoing training and company-wide initiatives to raise awareness. Before someone joins the Panopto team, we conduct criminal and credit background checks where local laws and regulations permit. All new team members are required to take information security and privacy awareness training. Developers are required to take secure coding training at the time of hire and periodically thereafter. Our security team conducts regular awareness and training activities, including security newsletters, email alerts, and phishing tests.
Panopto understands that strong governance is critical to an effective information security program. We have implemented a cross-functional Information Security Council representing all departments and teams to provide oversight and strategic direction to our security program. In addition, the Council promotes and provides business support necessary to integrate information security policies, standards, and best practices into the Company’s operations.

Application Security
From the point of capture to the point of playback, Panopto makes it easy to record, manage and stream your video content securely. As the leading video platform provider to the world’s largest organizations and most respected universities, we’ve invested heavily in product security, from the way users sign in to how we store and deliver video across the network.
Our video platform provides multi-layer security at the perimeter, within the repository, and during streaming. This ensures only authorized users can watch videos and data is safe at rest and in transit.
Panopto secures the video repository perimeter with support for multiple credential types, including OAuth, SAML 2.0, Active Directory, and a number of LMS ID providers. Our single sign-on (SSO) implementation supports rolling two-way synchronization of credentials, ensuring that user information is always up to date.
Within Panopto, users navigate and access videos, folders, and playlists through role-based permissions. These permissions can be configured for groups or individual users, providing granular control over video recording, live streaming, uploading, publishing, playback, and scheduling. Additional settings provide administrators with the ability to enforce strong passwords, password expiration, two-factor authentication via SSO, and session timeout.

Infrastructure Security
Panopto is hosted as a high-availability, redundant cluster across multiple AWS availability zones, eliminating single points of failure and providing additional platform reliability. Web, encoding, and database servers are mirrored across availability zones. In the event of an entire availability zone outage, the system seamlessly transitions to another zone, providing business continuity and protecting the integrity of your data.
AWS also provides significant protection against traditional network security vulnerabilities. For example, the threat of distributed denial of service (DDoS) attacks is mitigated through proprietary DDoS protection services and multi-homed AWS networks which provide internet access diversity. Man-in-the-middle (MITM) attacks are prevented through SSL-protected API endpoints. IP Spoofing is prevented through the AWS firewall infrastructure, which doesn’t permit instances to send traffic with a source IP or MAC address other than its own.
In addition, AWS maintains state-of-the-art, multi-perimeter physical security at their data centers. This includes prohibiting external access and not sharing the precise location of their data centers. Environmental safeguards include fire detection and suppression, fully redundant power systems, climate control, and real-time management of electrical and mechanical systems.
Operational Security
Panopto has adopted the NIST SP 800-53 control framework as the basis for operating a risk-based information security program. Our internal systems and processes are managed through security policies that cover the NIST control families, including access control, risk assessment, awareness and training, supply chain risk management, incident response, configuration management, and physical and environmental protection.
Our engineering team uses a secure software development lifecycle to ensure that security assurance activities such as code review and architecture analysis are inherent to the development effort.
We also perform quarterly vulnerability scans and regular internal audits of our cloud security practices and access rights. Each year, we partner with an internationally-known independent security firm to perform a comprehensive penetration test in order to identify exploitable vulnerabilities and minimize cyber-attack surface area.
In addition, Panopto values the assistance of outside researchers in helping to identify vulnerabilities in our products and services. Our Responsible Disclosure Program encourages researchers to report design and implementation issues that affect the confidentiality or integrity of user data or puts customer data at risk.
In the event of a security or business continuity incident, we maintain a response plan that covers all aspects of incident response, from preparation to identification, containment, eradication, recovery, and root cause analysis. The plan is exercised on an annual basis to ensure that we have a team of personnel trained to respond in order to minimize the impact of an incident and resume normal operations as quickly as possible.

Privacy
Panopto takes our responsibility to protect your personal information with care and respect seriously. Our approach to privacy begins with our commitment to give you transparency over the collection, use, and distribution of your data.
The EU General Data Protection Regulation (GDPR) brings consistency to data protection across Europe, built on the privacy principles of transparency, fairness, and accountability.
As a data processor, Panopto is committed to complying with the GDPR law.
This includes the use of encryption and anonymization to protect personal information, contracts with partners who play a role in our data processing, third-party audits of our data sources for PII, and adherence to the rights to access, information, rectification, erasure, data portability, objection, and restriction of processing.
Service Organization Control (SOC) 2 Compliance
Service Organization Control (SOC)
Developed by the American Institute of CPAs (AICPA), SOC defines criteria for managing customer data based on the five Trust Service Principles: security, availability, processing integrity, confidentiality, and privacy.
Panopto obtains an annual SOC 2 Type 2 audit by an independent third-party audit firm to assess the extent to which Panopto complies with the trust principle for security and availability:
- Security: The security principle refers to the protection of system resources against unauthorized access. Access controls are in place at Panopto and help prevent potential system abuse, theft, or unauthorized removal of data, misuse of software, and improper alteration or disclosure of information. IT security tools including network and web application firewalls, two-factor authentication, and intrusion detection used at Panopto are useful in preventing security breaches that can lead to unauthorized access of systems and data.
- Availability: The availability principle refers to the accessibility of the system, products, or services as stipulated by a contract or service level agreement. Monitoring network performance and availability, site failover, and security incident handling are critical in this context.
Our SOC 2 report is available to any partner, customer or prospect – but only if the recipient signs a Non-Disclosure Agreement (NDA) with Panopto. For more information, see:
Panopto Service Organization Control (SOC) 3 Report
Panopto’s SOC 3 report condenses the key information from the SOC 2 report into an easily digestible summary without signing an NDA.

Cloud Security Alliance (CSA) STAR Self-Assessment
The Cloud Security Alliance (CSA) is a nonprofit organization led by a broad coalition of industry practitioners, corporations, and other important stakeholders. It is dedicated to defining best practices to help ensure a more secure cloud computing environment, and to helping potential cloud customers make informed decisions when transitioning their IT operations to the cloud. Panopto has completed the CSA STAR Self-Assessment via the Consensus Assessments Initiative Questionnaire (CAIQ) and published the results to the CSA Security, Trust, and Assurance Registry: Panopto – CAIQ (v3.1).
Security Checklist
| Application Security | INCLUDED WITH PANOPTO |
|---|---|
| API authentication and encryption | Yes |
| Authentication policies | Yes |
| Data validation | Yes |
| Encryption at rest | Yes |
| Encryption in transit | Yes |
| Forensic analysis via audit logging | Yes |
| Hosted platform security | Yes |
| Infrastructure as code (IaC) | Yes |
| Logical content separation | Yes |
| Man-in-the-middle (MITM) prevention | Yes |
| Perimeter security and single-sign on (SSO) | Yes |
| Role-based authorization | Yes |
| Secure credential storage | Yes |
| Session timeouts | Yes |
| Video download prevention | Yes |
| Infrastructure and Operational Security | INCLUDED WITH PANOPTO |
|---|---|
| Adherence to widely recognized control framework | Yes |
| Risk management program | Yes |
| Background vetting of employees and contractors | Yes |
| Security and privacy awareness and training | Yes |
| Least privilege and separation of duties | Yes |
| Need-to-know access for confidential information | Yes |
| Secure software development lifecycle | Yes |
| Separation of operational, development, and staging environments | Yes |
| Monitoring and alerting for anomalous events | Yes |
| Regular control assessments and vulnerability scans | Yes |
| Annual third-party comprehensive penetration test | Yes |
| Risk-based prioritization of vulnerabilities for remediation | Yes |
| Secure media disposal | Yes |
| Malicious software protection | Yes |
| Data loss prevention | Yes |
| Physical and environmental controls | Yes |
| Incident management planning and testing | Yes |
| Business continuity and disaster recovery planning and testing | Yes |
| Capacity and resource planning | Yes |
| Privacy and Compliance | INCLUDED WITH PANOPTO |
|---|---|
| General Data Protection Regulation (GDPR) | Yes |
| SSAE 18 SOC 2 Type II | Yes |
| Cloud Security Alliance (CSA) STAR Self-Assessment | Yes |